Client server network – Client-server networks, the backbone of modern computing, are the unseen forces that power our daily digital interactions. This architecture, characterized by a central server providing services to multiple clients, is the foundation for countless applications we rely on, from browsing the web to managing our finances.
From the basic principles of communication to the intricacies of security and performance optimization, this exploration delves into the world of client-server networks, revealing how this powerful technology shapes our digital landscape.
Introduction to Client-Server Networks
Client-server networks are a fundamental architectural model in computer networking, defining how devices interact and share resources. This model is based on a hierarchical structure where dedicated servers provide services to multiple clients.
The client-server architecture establishes a clear division of responsibilities between clients and servers. Clients, typically user devices like computers, smartphones, or tablets, request services from servers. Servers, on the other hand, are powerful computers designed to handle requests from multiple clients simultaneously and provide the requested services.
Roles and Responsibilities of Clients and Servers
The roles and responsibilities of clients and servers in a network are distinct and interconnected.
- Clients: Clients are the entities that initiate requests for services. They are responsible for:
- Sending requests to the server.
- Receiving and processing responses from the server.
- Interacting with the user interface.
- Servers: Servers are the entities that provide services to clients. They are responsible for:
- Listening for and receiving client requests.
- Processing requests and providing the requested services.
- Managing resources and data.
- Ensuring security and access control.
Examples of Common Client-Server Applications
Client-server architecture is prevalent in numerous applications we encounter daily. Here are some common examples:
- Web Browsing: When you browse the internet, your web browser acts as a client, sending requests to web servers that host websites. The servers process these requests and send back the website’s content, which your browser displays.
- Email: Email services utilize client-server architecture. Your email client (e.g., Outlook, Gmail) acts as a client, connecting to an email server to send and receive emails.
- File Sharing: File sharing services like Dropbox and Google Drive rely on client-server architecture. You install a client application on your device, which connects to the service’s servers to store and access your files.
- Online Gaming: Online multiplayer games typically use client-server architecture. Players connect to game servers, which manage the game’s logic, player interactions, and world state.
- Databases: Database management systems often employ client-server architecture. Client applications connect to database servers to access, query, and manipulate data stored in the database.
Client-Server Communication
The core of client-server networks lies in the constant communication between clients and servers. This communication happens in a structured manner, using established protocols and a specific format.
Communication Process
The communication process between clients and servers involves a series of steps that ensure information exchange is reliable and efficient.
- Request: A client initiates the communication by sending a request to the server. This request can be anything from retrieving data (like a web page) to performing an action (like placing an order).
- Transmission: The client’s request is transmitted over the network, using protocols like TCP/IP.
- Reception: The server receives the client’s request and processes it.
- Response: The server then generates a response, which can include data, a confirmation message, or an error message.
- Transmission: The server transmits the response back to the client.
- Reception: The client receives the server’s response and processes it.
Protocols: TCP/IP and HTTP
Protocols are essential for structured communication between clients and servers. They define the rules and formats for exchanging information.
- TCP/IP (Transmission Control Protocol/Internet Protocol): This is a foundational protocol suite that enables communication over the internet. TCP provides reliable, ordered delivery of data, while IP handles the addressing and routing of packets.
- HTTP (Hypertext Transfer Protocol): This protocol is specifically designed for communication on the World Wide Web. It defines the format of requests and responses between web browsers (clients) and web servers.
Request-Response Cycles
The communication between clients and servers happens in a cyclical manner, where each request triggers a response.
The client initiates the communication by sending a request to the server, and the server responds accordingly.
This request-response cycle is fundamental to client-server interactions. It ensures that the client receives the necessary information or confirmation of the requested action.
Types of Client-Server Networks
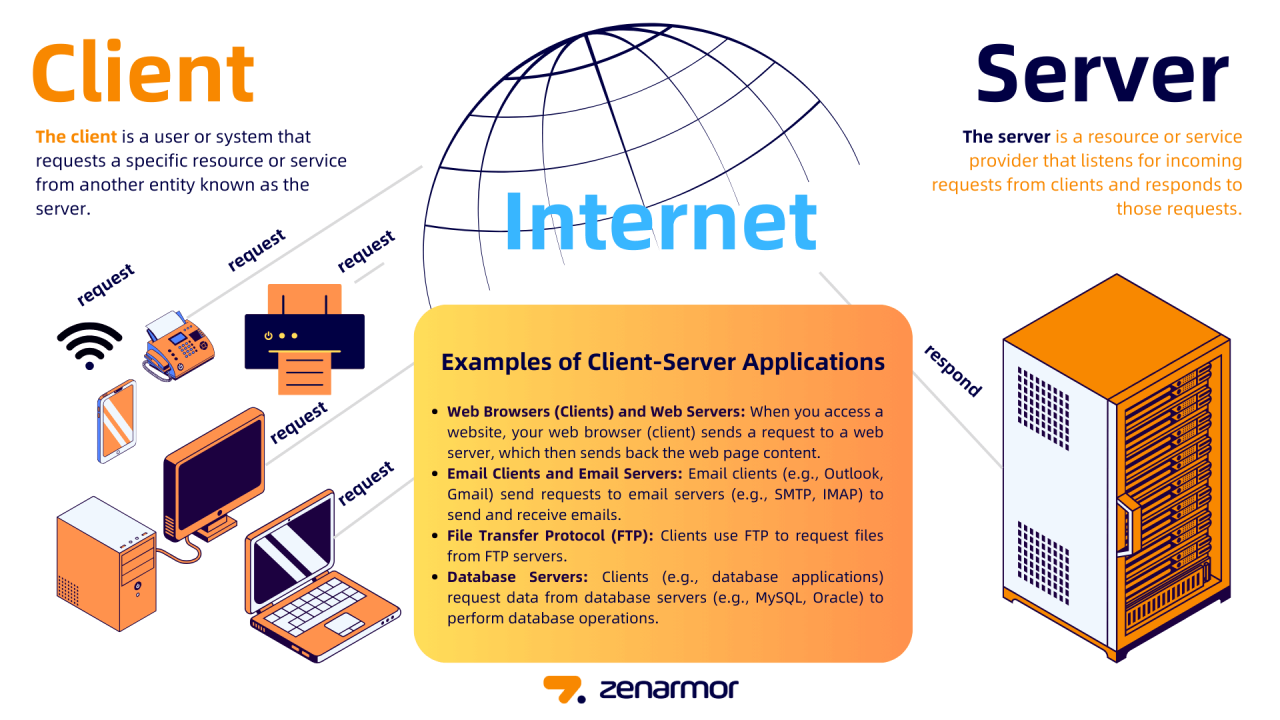
Client-server networks are ubiquitous in today’s digital world, powering everything from simple website browsing to complex online gaming. They come in various forms, each tailored to specific functionalities and purposes. This section delves into different types of client-server networks, highlighting their features, applications, and advantages and disadvantages.
Web Servers
Web servers are the foundation of the internet, responsible for serving web pages to users. They are the heart of the World Wide Web, allowing users to access and interact with websites.
- Features: Web servers process requests from clients (web browsers) and deliver HTML, CSS, JavaScript, and other files that form web pages. They also manage user authentication, session management, and dynamic content generation.
- Functionalities:
- Serving static content: Delivering files like HTML, CSS, images, and videos stored on the server.
- Serving dynamic content: Processing requests and generating content on the fly, often using server-side scripting languages like PHP, Python, or Ruby.
- Handling user authentication: Verifying user credentials and granting access to specific resources.
- Managing sessions: Tracking user interactions and maintaining state information across multiple requests.
- Applications: Web servers are used for a wide range of applications, including:
- E-commerce: Providing online stores for purchasing goods and services.
- Social media: Hosting platforms like Facebook, Twitter, and Instagram.
- Content management systems: Enabling websites with dynamic content and user-generated content.
- Online banking: Providing secure access to financial accounts and transactions.
- Advantages:
- Centralized management: Easier to update and maintain content and applications.
- Scalability: Web servers can be easily scaled to handle increasing traffic and user demands.
- Security: Centralized security measures can be implemented to protect data and resources.
- Disadvantages:
- Single point of failure: If the web server fails, the entire website becomes inaccessible.
- Complexity: Configuring and managing web servers can be complex, requiring specialized knowledge.
Email Servers
Email servers are responsible for sending, receiving, and storing emails. They play a crucial role in communication and information exchange in the digital age.
- Features: Email servers handle email routing, message storage, and spam filtering. They also manage user accounts and provide features like email forwarding and aliases.
- Functionalities:
- Sending emails: Accepting email messages from clients and delivering them to recipients.
- Receiving emails: Retrieving emails from other servers and storing them for users.
- Storing emails: Maintaining email messages in user inboxes and providing access for retrieval.
- Filtering spam: Identifying and blocking unwanted or malicious emails.
- Applications: Email servers are used for various purposes, including:
- Personal email: Providing email accounts for individuals.
- Business email: Enabling communication within organizations and with external clients.
- Marketing email campaigns: Sending promotional emails to target audiences.
- Advantages:
- Reliable communication: Emails are typically delivered reliably and efficiently.
- Scalability: Email servers can handle large volumes of email traffic.
- Centralized management: Managing email accounts and settings is centralized.
- Disadvantages:
- Security concerns: Email servers can be vulnerable to spam and phishing attacks.
- Complexity: Setting up and maintaining email servers can be complex.
File Servers
File servers are dedicated to storing and sharing files among users on a network. They provide a central location for storing data and ensure its accessibility to authorized users.
- Features: File servers offer file storage, sharing, and access control. They often provide features like file versioning, backups, and security measures to protect data.
- Functionalities:
- File storage: Providing a centralized location for storing files and documents.
- File sharing: Allowing users to access and share files with others on the network.
- Access control: Restricting access to specific files or folders based on user permissions.
- File versioning: Keeping track of different versions of files and allowing users to revert to previous versions.
- Backups: Regularly creating copies of data to prevent data loss in case of failures.
- Applications: File servers are widely used in various settings, including:
- Business networks: Storing and sharing company documents, presentations, and other files.
- Home networks: Sharing files and documents among family members.
- Educational institutions: Providing students and faculty with access to shared resources.
- Advantages:
- Centralized data storage: Easier to manage and backup data.
- File sharing: Simplifies collaboration and information sharing.
- Security: Access control features protect data from unauthorized access.
- Disadvantages:
- Single point of failure: If the file server fails, all data becomes inaccessible.
- Performance issues: Large file servers can experience performance bottlenecks.
Server-Side Technologies
The server side of a client-server network is where the magic happens. It’s responsible for handling requests from clients, processing data, and sending back responses. This section delves into the technologies that power the server side, focusing on programming languages, databases, and common technologies for managing client requests and data.
Server-Side Programming Languages and Frameworks
Server-side programming languages are the foundation of server-side applications. They enable developers to write code that executes on the server, handling client requests and managing data. Here are some popular languages and frameworks:
- Java: A robust and widely used language known for its platform independence and enterprise-level applications. Popular frameworks include Spring and Jakarta EE.
- Python: A versatile language popular for its readability and extensive libraries. Frameworks like Django and Flask provide robust tools for building web applications.
- Node.js: A JavaScript runtime environment that enables developers to build fast and scalable server-side applications. Popular frameworks include Express.js and NestJS.
The Role of Databases
Databases are essential components of client-server systems. They store and manage the data that applications need to function.
- Relational Databases (RDBMS): These databases organize data in tables with rows and columns, providing structured data storage. Popular examples include MySQL, PostgreSQL, and Oracle.
- NoSQL Databases: These databases offer more flexibility in data structure and are suitable for handling large volumes of unstructured data. Examples include MongoDB, Cassandra, and Redis.
Server-Side Technologies for Handling Client Requests and Managing Data
Server-side technologies handle the complex tasks of processing client requests, managing data, and sending responses.
- Web Servers: These servers act as intermediaries between clients and web applications. They receive client requests, process them, and send back responses. Popular web servers include Apache HTTP Server and Nginx.
- Application Servers: These servers handle the execution of web applications, providing a runtime environment for server-side code. Popular examples include Tomcat, JBoss, and WebSphere.
- API (Application Programming Interface): APIs define how different software components interact. They allow client applications to communicate with server-side applications and access data.
Client-Side Technologies
Client-side technologies are the tools and languages that power the interactive and dynamic aspects of websites and web applications. They are responsible for how users experience a website, from the layout and visual design to the interactive elements and the display of server-generated content.
Web Browsers
Web browsers act as the intermediary between users and the server. They interpret the code received from the server and render the content on the user’s screen. They are essentially the gateway to the internet, allowing users to access and interact with web resources.
Popular Client-Side Technologies
Client-side technologies are essential for creating engaging and interactive web experiences. They empower developers to build dynamic and responsive websites.
- HTML (HyperText Markup Language) is the foundation of web pages. It defines the structure and content of a web page, using tags to create elements like headings, paragraphs, images, and links.
- CSS (Cascading Style Sheets) controls the visual presentation of web pages. It determines elements’ colors, fonts, sizes, spacing, and overall layout.
- JavaScript is a scripting language that adds interactivity and dynamic behavior to web pages. It enables features like form validation, animations, and real-time updates without requiring page reloads.
Client-Side Technologies Enable User Interaction
Client-side technologies play a crucial role in enabling user interaction and displaying server-generated content. They bridge the gap between the user’s actions and the server’s responses, making websites dynamic and responsive.
- Form Submission: JavaScript can validate user input in forms before submission, ensuring data accuracy and preventing errors. When a form is submitted, the browser sends the data to the server for processing.
- Dynamic Content Updates: JavaScript can fetch and update content on a web page without requiring a full page reload. This creates a seamless and interactive experience for users. For example, updating a shopping cart without refreshing the entire page.
- User Interface (UI) Elements: JavaScript can create interactive UI elements like buttons, sliders, and dropdowns. These elements enhance user engagement and make websites more intuitive to navigate.
Security Considerations: Client Server Network
Client-server networks, while offering numerous advantages, are also susceptible to various security threats. Understanding these vulnerabilities and implementing appropriate security measures is crucial to ensure the integrity, confidentiality, and availability of data and resources.
Common Security Threats and Vulnerabilities
Client-server networks face a range of security threats, including:
- Data Breaches: Unauthorized access to sensitive data stored on servers can lead to data theft, misuse, or corruption. This can occur through various means, including hacking, malware infections, or insider threats.
- Denial-of-Service (DoS) Attacks: These attacks aim to disrupt the availability of network services by overwhelming servers with excessive traffic, making them unresponsive to legitimate requests. This can impact critical business operations and cause financial losses.
- Malware Infections: Malicious software, such as viruses, worms, and ransomware, can compromise client-server systems, steal data, or disrupt network operations. These infections can spread through various channels, including email attachments, malicious websites, or software vulnerabilities.
- Man-in-the-Middle (MitM) Attacks: These attacks involve an attacker intercepting communication between clients and servers, potentially eavesdropping on data or manipulating information exchanged. This can compromise user authentication and data integrity.
- SQL Injection: This technique exploits vulnerabilities in web applications to manipulate backend databases, potentially allowing attackers to access or modify sensitive data. This can be achieved by injecting malicious SQL code into input fields.
- Cross-Site Scripting (XSS): This vulnerability allows attackers to inject malicious scripts into web pages viewed by other users. This can lead to data theft, unauthorized actions, or the spread of malware.
Security Measures and Best Practices
To mitigate these threats, several security measures and best practices can be implemented:
- Encryption: Encrypting data in transit and at rest using strong algorithms like AES-256 ensures confidentiality and protects data from unauthorized access. This involves encrypting data during transmission between clients and servers and storing sensitive data in encrypted form on servers.
- Authentication: Strong authentication mechanisms, such as multi-factor authentication (MFA), help verify user identities and prevent unauthorized access. This involves requiring users to provide multiple forms of authentication, such as passwords, one-time codes, or biometrics, to gain access to network resources.
- Access Control: Implementing robust access control mechanisms restricts user access to specific resources based on their roles and permissions. This ensures that only authorized users can access sensitive data and perform specific actions on the network. Access control lists (ACLs) and role-based access control (RBAC) are commonly used techniques for implementing access control.
- Regular Security Audits: Regularly auditing network systems and applications for vulnerabilities helps identify and address potential security risks. This involves scanning for known vulnerabilities, reviewing system configurations, and testing security controls. Regular audits ensure that security measures are effective and up-to-date.
- Firewall Protection: Firewalls act as a barrier between a network and external threats, blocking unauthorized access and filtering incoming and outgoing traffic. Firewalls can be implemented at various levels, including network-level firewalls, host-based firewalls, and application-level firewalls.
- Intrusion Detection and Prevention Systems (IDS/IPS): These systems monitor network traffic for suspicious activity and alert administrators or take automatic actions to prevent attacks. IDS detect and log suspicious activities, while IPS actively block or mitigate attacks. They play a crucial role in detecting and responding to network threats.
- Regular Software Updates: Regularly updating software and operating systems patches vulnerabilities and improves system security. Software vendors release updates to address known security flaws, so keeping systems updated is essential to protect against exploits.
- User Awareness Training: Educating users about common security threats and best practices helps minimize the risk of human error. This includes training users on phishing scams, password security, and safe browsing practices. User awareness training plays a significant role in preventing social engineering attacks and reducing the likelihood of users becoming victims of security breaches.
- Data Backup and Recovery: Regularly backing up critical data and implementing disaster recovery plans helps minimize the impact of data loss or system failures. This ensures that data can be restored in case of a security breach or system outage. Regular backups and disaster recovery plans are crucial for business continuity and data protection.
Network Topology and Architecture
Network topology and architecture play crucial roles in the performance and scalability of client-server networks. Topology refers to the physical or logical arrangement of network components, while architecture defines the overall structure and organization of the network.
Network Topologies
Network topology determines how devices are connected and how data flows within the network. Common topologies used in client-server networks include:
- Star Topology: In a star topology, all devices connect to a central hub or switch. This topology is simple to manage and troubleshoot, and it provides centralized control. However, if the central device fails, the entire network becomes inoperable.
- Bus Topology: In a bus topology, all devices are connected to a single shared cable. This topology is inexpensive and easy to install, but it can suffer from performance bottlenecks and signal interference. If the cable fails, the entire network is affected.
- Ring Topology: In a ring topology, devices are connected in a closed loop. Data travels in one direction around the ring. This topology offers high bandwidth and fault tolerance, as data can be rerouted if one device fails. However, it can be complex to manage and troubleshoot.
Network Architecture
Network architecture defines the overall structure and organization of the network, including the components, protocols, and services used. A well-designed architecture ensures efficient data flow, scalability, and security. Common network architectures used in client-server networks include:
- Two-Tier Architecture: This architecture consists of a client tier and a server tier. Clients interact directly with servers, providing a simple and efficient solution for small networks. However, it can become a bottleneck as the number of clients increases.
- Three-Tier Architecture: This architecture adds a middle tier between the client and server tiers. The middle tier acts as a load balancer and application server, handling requests from clients and distributing them to appropriate servers. This architecture offers improved scalability and performance compared to two-tier architectures.
- N-Tier Architecture: This architecture extends the three-tier architecture to include multiple tiers, each performing specific tasks. This allows for more complex applications and better scalability. However, it can become complex to manage and troubleshoot.
Hypothetical Client-Server Network Architecture
Consider a hypothetical client-server network architecture for an online e-commerce platform:
| Component | Description | Connections |
|---|---|---|
| Client Tier | Web browsers, mobile apps, and other devices used by customers to access the e-commerce platform. | Connects to the load balancer through the internet. |
| Load Balancer | Distributes client requests to multiple web servers. | Connects to the web servers and the database server. |
| Web Server Tier | Handles client requests and serves web pages, images, and other content. | Connects to the database server and the application server. |
| Application Server Tier | Handles business logic and data processing. | Connects to the database server. |
| Database Server Tier | Stores and manages customer data, product information, and order details. | Connects to the web server tier, the application server tier, and the database server. |
Performance Optimization
In a client-server network, optimizing performance is crucial for delivering a seamless user experience and ensuring efficient data transfer. Several factors can impact performance, and implementing effective strategies can significantly improve network efficiency.
Factors Affecting Performance, Client server network
Various factors can influence the performance of a client-server network. These factors include:
- Network Bandwidth: The amount of data that can be transferred per unit of time over a network connection directly affects performance. Limited bandwidth can lead to slow loading times and delays in data transmission.
- Network Latency: The time it takes for a data packet to travel from the client to the server and back can significantly impact user experience, especially for real-time applications. High latency can cause lag and interruptions.
- Server Processing Power: The server’s ability to handle requests efficiently is crucial for performance. Insufficient processing power can lead to delays in responding to client requests.
- Database Performance: The efficiency of the database used by the server plays a significant role in overall performance. Slow database queries can hinder the server’s ability to respond promptly to client requests.
- Client Hardware: The capabilities of the client device, such as its processing power, memory, and network connection, can influence its ability to interact with the server effectively. A slow or outdated client device may experience performance issues.
- Network Congestion: When too much data is being transmitted over a network at the same time, it can lead to congestion, causing delays and packet loss.
- Application Design: The design and implementation of the client-server application can significantly impact performance. Inefficient code or poor design choices can lead to performance bottlenecks.
Caching
Caching is a technique used to store frequently accessed data in a temporary location, closer to the client, to reduce the need to fetch data from the server repeatedly. This significantly improves performance by reducing network traffic and latency.
- Browser Caching: Web browsers cache static content like images, CSS files, and JavaScript files, reducing the need to download them repeatedly on subsequent visits to the same website.
- Server-Side Caching: Servers can cache dynamic content, such as database results or API responses, to reduce the processing load and improve response times.
- Content Delivery Networks (CDNs): CDNs are distributed networks of servers that cache content closer to users, minimizing latency and improving performance, especially for geographically dispersed users.
Load Balancing
Load balancing distributes incoming client requests across multiple servers, preventing any single server from becoming overloaded. This technique helps ensure consistent performance and prevents service disruptions.
- Round Robin: This method distributes requests to servers in a circular order, ensuring each server receives an equal share of the workload.
- Least Connections: This method directs requests to the server with the fewest active connections, minimizing the load on individual servers.
- Weighted Round Robin: This method allows assigning weights to servers based on their capacity, ensuring servers with higher processing power handle more requests.
Content Delivery Networks (CDNs)
CDNs are networks of geographically distributed servers that cache content closer to users, reducing latency and improving performance. They are particularly effective for delivering static content like images, videos, and JavaScript files.
- Edge Caching: CDNs store content in servers located at the network edge, closer to users, minimizing the distance data needs to travel.
- Global Content Delivery: CDNs offer global coverage, ensuring content is served from the closest server to users, regardless of their location.
- Dynamic Content Optimization: CDNs can also optimize dynamic content, such as website pages, by caching them in their edge servers.
Techniques for Reducing Latency
Various techniques can be employed to minimize latency and enhance user experience. These include:
- Minimizing HTTP Requests: Reducing the number of HTTP requests required to load a webpage can significantly improve performance by reducing the time spent waiting for responses from the server.
- Optimizing Image Sizes: Compressing images without compromising quality can significantly reduce file sizes, leading to faster loading times.
- Using Asynchronous Loading: Loading resources asynchronously, such as scripts and images, allows the browser to continue rendering the page while those resources are being loaded, improving perceived performance.
- Implementing Server-Side Rendering: Rendering pages on the server before sending them to the client can reduce the amount of JavaScript required on the client side, improving performance.
- Using WebSockets: WebSockets provide a persistent connection between the client and server, enabling real-time communication and reducing the need for frequent HTTP requests.
Real-World Applications
Client-server networks are the backbone of countless modern services and applications, profoundly shaping our daily lives and the digital landscape. They provide a robust and scalable framework for delivering information, resources, and services to a vast user base.
E-commerce
E-commerce platforms heavily rely on client-server networks. When a customer browses an online store, their web browser acts as the client, requesting product information and images from the server. The server processes the request, retrieves the data, and sends it back to the client, displaying the website on the customer’s screen. The server also handles payment processing, order management, and inventory tracking, ensuring a seamless shopping experience.
Online Banking
Online banking services utilize client-server networks to provide secure access to financial accounts. Users log in to their bank’s website or mobile app (the client) to access their accounts, with the server managing all the transactions, data, and security measures. The server verifies user credentials, processes payments, and keeps track of account balances. This allows users to perform banking transactions conveniently from any location with internet access.
Social Media
Social media platforms like Facebook, Twitter, and Instagram heavily rely on client-server networks to connect users and share information. Users access these platforms through their web browsers or mobile apps (the clients), interacting with the server. The server manages user profiles, posts, messages, and interactions, facilitating communication and information sharing among millions of users.
Other Modern Services
Client-server networks are essential for various other modern services, including:
- Streaming Services: Platforms like Netflix, Spotify, and YouTube use client-server networks to deliver streaming content to users. Users access the service through their devices (clients), requesting content from the server, which then streams it to their devices.
- Cloud Storage: Services like Google Drive, Dropbox, and OneDrive utilize client-server networks to store and manage data remotely. Users access their data through client applications, with the server storing and managing all the files.
- Email Services: Email services like Gmail, Outlook, and Yahoo Mail rely on client-server networks to send and receive emails. Users access their email accounts through their email clients, with the server managing email storage, delivery, and retrieval.
- Gaming: Online multiplayer games rely heavily on client-server networks to connect players and facilitate gameplay. The server manages the game world, player interactions, and communication, while players access the game through their clients.
Last Word
Understanding client-server networks is crucial for anyone seeking to navigate the digital world. From comprehending how websites function to appreciating the security measures that protect our online interactions, the knowledge gained from exploring this architecture empowers us to become more informed and confident digital citizens.
Client-server networks are the backbone of modern computing, allowing devices to communicate and share resources. A key element in this architecture is the server, which acts as a central hub for data and services. One specific type of server, an OPC UA server , is designed for industrial automation, facilitating seamless data exchange between different systems and applications within a manufacturing environment.