Outline server – Artikel Server: A Comprehensive Guide delves into the intricate world of servers, unveiling their essential role in modern computing. This guide takes you on a journey from the fundamental definition of servers and their purpose to exploring the diverse types, features, and functionalities that power our digital lives. Prepare to uncover the complexities of server implementation, configuration, and management, while gaining insights into their impactful applications across various industries.
From physical servers to cloud-based solutions, we explore the advantages and disadvantages of each type, highlighting the essential features that drive network security, performance, and scalability. This guide equips you with the knowledge to navigate the intricacies of server technology, providing practical insights for both beginners and experienced users.
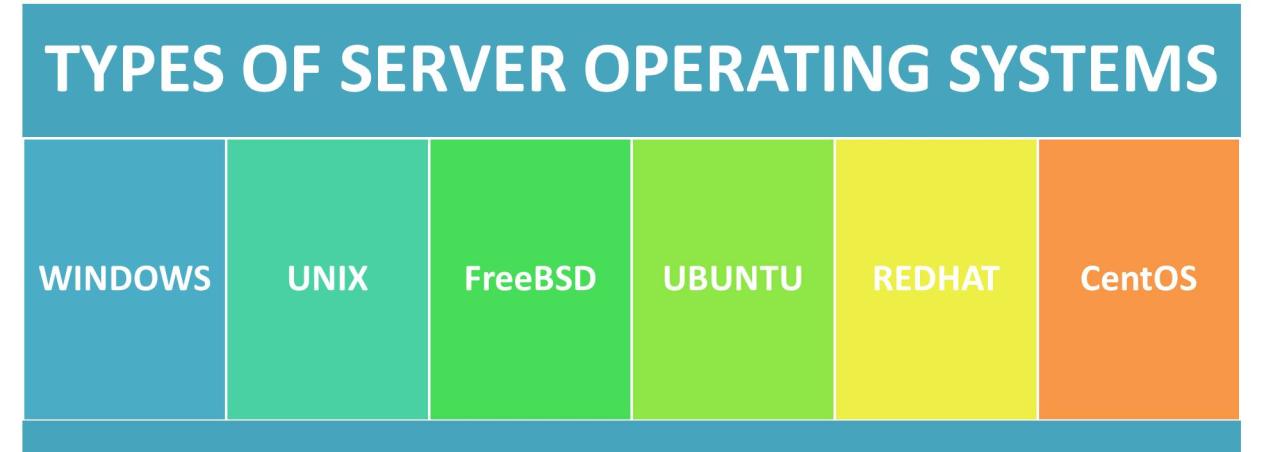
Features and Functionality

Artikel servers offer a comprehensive suite of features that enhance network security, performance, and manageability. These servers are designed to provide a secure and reliable foundation for businesses and organizations of all sizes.
Routing
Routing is a fundamental aspect of network communication, and Artikel servers play a crucial role in directing network traffic. Artikel servers can be configured to act as routers, enabling them to forward packets between different networks and devices. This capability is essential for connecting multiple subnets, creating virtual private networks (VPNs), and establishing secure communication channels.
Firewalling
Artikel servers provide robust firewall capabilities to protect networks from unauthorized access and malicious attacks. Firewalls act as a barrier between a network and the outside world, inspecting incoming and outgoing traffic based on predefined rules. Artikel servers can be configured with advanced firewall rules to block specific ports, protocols, and IP addresses, effectively preventing unauthorized access and mitigating security risks.
VPN
Artikel servers enable the creation of virtual private networks (VPNs), providing secure and encrypted connections between devices over public networks. VPNs establish a secure tunnel between a client device and a server, ensuring that all data transmitted through the tunnel is encrypted and protected from eavesdropping. This is particularly important for remote workers, mobile devices, and sensitive data transmission.
DNS
Artikel servers can function as DNS servers, providing name resolution services for network devices. DNS servers translate human-readable domain names into numerical IP addresses, enabling devices to communicate with each other. Artikel servers can be configured as primary or secondary DNS servers, offering reliable and secure name resolution services for networks.
Implementation and Configuration
Setting up and configuring an Artikel server involves several steps, ensuring a secure and efficient environment for your data. This section will guide you through the process, highlighting best practices and essential configurations.
Server Setup and Configuration
- Software Installation: Begin by installing the Artikel server software on your chosen operating system. The official Artikel website provides detailed instructions and downloadable packages for various platforms, including Linux, macOS, and Windows.
- Configuration File: Once installed, locate the configuration file, typically named “config.json.” This file contains settings for the server, including ports, network interfaces, and security protocols. Modify the file to customize your server’s behavior.
- Access Control: Set up access control rules to define who can connect to your server. You can use IP address restrictions, user accounts, or other authentication methods to control access.
- Network Configuration: Configure your network to allow traffic to and from the Artikel server. This might involve setting up port forwarding rules on your router or firewall.
- Client Setup: Once the server is running, you can set up clients to connect to it. The Artikel website offers detailed instructions and guides for configuring clients on various devices, including computers, smartphones, and tablets.
Security Best Practices
- Strong Passwords: Use strong and unique passwords for your server and any user accounts you create.
- Regular Updates: Keep your server software up to date with the latest security patches to protect against vulnerabilities.
- Firewall Configuration: Implement a robust firewall to restrict unauthorized access to your server. Configure rules to block unnecessary traffic and allow only authorized connections.
- Encryption: Use strong encryption protocols, such as TLS/SSL, to secure communication between the server and clients.
- Two-Factor Authentication: Enable two-factor authentication (2FA) for your server and user accounts to add an extra layer of security.
Resource Management
- Monitoring: Monitor your server’s performance and resource usage regularly to identify any potential issues. Tools like system monitoring dashboards can help track CPU, memory, and network activity.
- Resource Allocation: Allocate resources appropriately based on your server’s workload. You can adjust settings like CPU and memory limits to ensure optimal performance.
- Data Backup: Implement regular backups of your server’s data to protect against data loss due to hardware failure or other incidents.
- Security Audits: Conduct periodic security audits to identify and address any vulnerabilities or weaknesses in your server’s configuration.
Configuration Options
| Option | Description | Impact |
|---|---|---|
| Port | Specifies the port on which the server listens for connections. | Changing the port can affect client connections and firewall rules. |
| Network Interface | Determines the network interface used by the server. | Selecting the correct interface ensures proper network connectivity. |
| Encryption Protocol | Specifies the encryption protocol used for secure communication. | Choosing a strong encryption protocol enhances security. |
| Access Control Rules | Define who can connect to the server based on IP addresses, user accounts, or other criteria. | Access control rules restrict unauthorized access to the server. |
| Log Level | Sets the level of detail for server logs. | Higher log levels provide more detailed information for troubleshooting. |
Use Cases and Applications
Artikel servers are versatile tools that find applications in various industries and settings, playing a crucial role in enabling seamless operations and providing essential services. From powering large-scale enterprises to facilitating personal tasks at home, Artikel servers offer a wide range of use cases.
Business Applications
Artikel servers are integral to the smooth functioning of businesses of all sizes. They provide a centralized platform for managing data, applications, and resources, facilitating efficient operations and improved productivity.
- File Sharing and Collaboration: Businesses can use Artikel servers to create secure and reliable file-sharing platforms, enabling teams to collaborate on projects, share documents, and access data from anywhere. This facilitates efficient teamwork and reduces reliance on external services.
- Email and Communication: Artikel servers power email systems, ensuring secure and reliable communication within organizations. They also provide a platform for managing email lists, automating tasks, and integrating with other business applications.
- Website Hosting: Artikel servers are essential for hosting websites, providing the necessary infrastructure for website content, applications, and databases. Businesses can leverage servers to create and manage their online presence, ensuring scalability and reliability.
- Data Management and Storage: Artikel servers provide a centralized location for storing and managing critical business data, ensuring data security, integrity, and accessibility. Businesses can utilize servers to implement robust data backup and disaster recovery plans, safeguarding valuable information.
- Application Hosting: Artikel servers are used to host various business applications, including CRM, ERP, and accounting software. This allows businesses to access and manage applications from anywhere, improving efficiency and productivity.
Organizational Applications
Artikel servers are essential for organizations of all types, from government agencies to non-profit organizations, providing the infrastructure for managing critical operations and serving their constituents.
- Public Services: Artikel servers power government websites, providing citizens with access to public information, services, and online transactions. They also support essential government functions, such as data management, communication, and security.
- Education: Educational institutions rely on Artikel servers for managing student records, online learning platforms, and administrative tasks. They provide a secure and reliable platform for delivering educational resources and facilitating communication between students, faculty, and staff.
- Healthcare: Artikel servers play a vital role in healthcare organizations, enabling secure data storage and management of patient records, electronic health records (EHRs), and medical imaging. They also support telemedicine applications, facilitating remote patient care and diagnosis.
- Non-Profit Organizations: Artikel servers help non-profit organizations manage their operations, including fundraising, donor management, and communication. They provide a platform for online donations, event management, and outreach activities.
Home Applications
Artikel servers are not limited to businesses and organizations; they also have a wide range of applications in homes, providing individuals with enhanced functionality and control over their digital lives.
- Media Server: Artikel servers can be used as media servers, centralizing and storing music, videos, and photos, allowing users to access their media library from any device in their home network. This provides a convenient way to enjoy entertainment content and share media with family and friends.
- Home Automation: Artikel servers can be used to control and manage smart home devices, including lighting, thermostats, security systems, and appliances. This allows users to automate tasks, create custom routines, and enhance their home’s energy efficiency.
- Backup and Storage: Artikel servers can be used as a secure and reliable platform for backing up important data from personal computers, smartphones, and other devices. This safeguards against data loss due to hardware failure, accidental deletion, or malware attacks.
- Remote Access: Artikel servers enable users to access their home computers and files remotely, allowing them to work from anywhere, manage their finances, or access important documents while traveling.
Benefits of Using an Artikel Server
Artikel servers offer a compelling set of advantages that can significantly enhance network performance, security, and overall efficiency. They streamline network management, reduce costs, and provide a robust foundation for various applications.
Enhanced Security
Artikel servers play a crucial role in bolstering network security. They act as a central point of control, enabling administrators to enforce granular access policies and monitor network activity effectively. By implementing strong authentication measures and firewalls, Artikel servers effectively mitigate threats and protect sensitive data.
Improved Performance
Artikel servers can significantly improve network performance by optimizing traffic flow and reducing latency. They act as a centralized hub for network resources, enabling efficient data routing and minimizing bottlenecks. This optimized traffic management results in faster data transmission and improved application responsiveness.
Scalability and Flexibility
Artikel servers provide exceptional scalability and flexibility, adapting seamlessly to evolving network demands. They can be easily scaled up or down to accommodate fluctuating traffic volumes, ensuring optimal performance even during peak periods. This adaptability makes Artikel servers ideal for businesses experiencing rapid growth or facing unpredictable traffic patterns.
Simplified Network Management
Artikel servers streamline network management by centralizing control over network resources. Administrators can easily configure and manage network settings, monitor performance, and troubleshoot issues from a single interface. This centralized approach simplifies complex network operations and reduces the time and effort required for maintenance.
Cost Savings
Artikel servers can contribute to significant cost savings by optimizing network resource utilization. They eliminate the need for multiple standalone servers, reducing hardware costs and simplifying infrastructure management. Additionally, their centralized management capabilities reduce the need for specialized personnel, further minimizing operational expenses.
Real-World Examples, Outline server
– Large Enterprises: Artikel servers are widely deployed in large enterprises to manage complex networks and secure sensitive data. For example, financial institutions utilize Artikel servers to protect customer transactions and maintain compliance with regulatory requirements.
– Educational Institutions: Educational institutions rely on Artikel servers to manage their network infrastructure, provide secure access to online resources, and facilitate collaboration among students and faculty.
– Healthcare Organizations: Healthcare organizations leverage Artikel servers to ensure the security and integrity of patient data, comply with HIPAA regulations, and support critical medical applications.
Challenges and Considerations: Outline Server
While Artikel servers offer numerous benefits, they also present certain challenges and considerations that users should be aware of. Understanding these factors is crucial for making informed decisions about using Artikel servers and mitigating potential risks.
Factors to Consider When Choosing an Artikel Server Solution
The choice of an Artikel server solution depends on various factors, including the specific needs, technical expertise, and budget of the user. Some key considerations include:
- Server Location and Jurisdiction: The location of the server can impact privacy and security, as different jurisdictions have varying data retention and privacy laws. For example, servers located in countries with strict surveillance laws might pose higher risks to user privacy.
- Server Performance and Capacity: The server’s performance and capacity should be sufficient to handle the expected traffic and data volume. Factors like processing power, storage space, and bandwidth are crucial for a smooth user experience.
- Security Features and Protocols: The server should offer robust security features, such as encryption, authentication, and access control, to protect user data from unauthorized access. Secure protocols like HTTPS and VPN should be implemented to ensure secure communication.
- Cost and Maintenance: Setting up and maintaining an Artikel server can involve costs, including server hardware, software licenses, and ongoing maintenance. Users should carefully evaluate these costs before making a decision.
- Technical Expertise: Managing and configuring an Artikel server requires a certain level of technical expertise. Users with limited technical knowledge might need to seek assistance from experts or choose managed server solutions.
Mitigating Risks and Overcoming Potential Issues
To mitigate risks and overcome potential issues associated with using Artikel servers, users can implement several strategies:
- Regular Security Audits: Regularly auditing the server’s security configuration and software updates can help identify and address vulnerabilities promptly.
- Strong Passwords and Two-Factor Authentication: Using strong passwords and enabling two-factor authentication for accessing the server can significantly enhance security.
- Regular Backups: Creating regular backups of critical data can help recover from data loss or system failures.
- Monitoring and Alerting: Implementing monitoring and alerting systems can help detect anomalies and potential security threats early on.
- Staying Informed: Staying informed about the latest security threats and best practices is crucial for maintaining a secure server environment.
Future Trends in Servers
The server landscape is constantly evolving, driven by advancements in technology and changing user demands. From the rise of cloud computing to the increasing adoption of virtualization, these trends are shaping the future of servers and their role in network environments.
Impact of Cloud Computing and Virtualization
Cloud computing and virtualization have revolutionized the way servers are deployed and managed. They offer several advantages, including:
* Increased Flexibility and Scalability: Cloud-based servers can be easily scaled up or down to meet fluctuating demands, allowing organizations to optimize resource utilization and reduce costs.
* Reduced Infrastructure Costs: Cloud providers handle the infrastructure management, reducing the need for organizations to invest in hardware and maintenance.
* Improved Accessibility and Collaboration: Cloud servers are accessible from anywhere with an internet connection, enabling seamless collaboration and remote access.
Virtualization, on the other hand, allows multiple operating systems and applications to run on a single physical server, maximizing resource utilization and reducing hardware costs.
Future Role of Servers in Evolving Network Environments
Servers are expected to play a crucial role in evolving network environments, driven by emerging trends such as:
* Edge Computing: Edge computing brings computation and data storage closer to users, reducing latency and improving performance. Servers will play a critical role in supporting edge computing applications, enabling real-time data processing and analysis.
* Internet of Things (IoT): The proliferation of IoT devices will generate massive amounts of data, requiring robust server infrastructure to handle data storage, processing, and analysis.
* Artificial Intelligence (AI): AI applications demand significant computing power and data storage capabilities, making servers a vital component in supporting AI workloads.
* 5G and Beyond: The advent of 5G and future wireless technologies will enable faster data transfer speeds and increased bandwidth, requiring servers to handle higher data volumes and processing demands.
Servers will continue to evolve to meet these emerging trends, with a focus on:
* Increased Processing Power: Servers will need to handle increasingly complex workloads, requiring more powerful processors and larger memory capacities.
* Enhanced Security: As network environments become more complex, servers will need to incorporate robust security features to protect sensitive data.
* Improved Energy Efficiency: With growing concerns about sustainability, servers will be designed to optimize energy consumption and reduce their environmental impact.
“The future of servers lies in their ability to adapt to the changing demands of modern network environments, offering increased performance, scalability, security, and energy efficiency.”
Best Practices for Server Management
Managing and maintaining a server effectively is crucial for ensuring optimal performance, security, and reliability. This involves a comprehensive approach encompassing various aspects, from regular monitoring to proactive security measures.
Server Monitoring
Monitoring server performance is essential for identifying potential issues before they escalate into major problems. Regularly tracking key metrics such as CPU utilization, memory usage, disk space, and network traffic provides valuable insights into server health.
- Utilize monitoring tools to track critical server metrics and receive alerts for any anomalies.
- Establish clear thresholds for performance indicators, enabling early detection of potential issues.
- Implement a system for logging server events, facilitating troubleshooting and analysis.
Troubleshooting Issues
Troubleshooting server issues requires a systematic approach to pinpoint the root cause and implement appropriate solutions.
- Maintain detailed logs to trace the timeline of events and identify potential sources of errors.
- Utilize diagnostic tools to gather relevant information about the issue, such as system logs, network traces, and performance metrics.
- Isolate the problem by systematically eliminating potential causes through testing and experimentation.
Server Security
Maintaining a secure server environment is paramount to protect sensitive data and prevent unauthorized access.
- Implement strong passwords and access control mechanisms to restrict unauthorized access to the server.
- Regularly update operating systems and software to patch vulnerabilities and enhance security.
- Utilize firewalls and intrusion detection systems to monitor network traffic and block malicious activity.
Regular Updates
Keeping servers updated with the latest security patches and software releases is crucial for mitigating vulnerabilities and ensuring optimal performance.
- Establish a schedule for regular updates and ensure that all necessary updates are applied promptly.
- Test updates in a staging environment before deploying them to the production server to minimize potential disruptions.
- Maintain a record of all updates applied to the server for future reference and troubleshooting.
Backups and Disaster Recovery
Data backups and disaster recovery plans are essential for mitigating the impact of unforeseen events such as hardware failures, natural disasters, or cyberattacks.
- Implement a comprehensive backup strategy that includes regular backups of critical data and system configurations.
- Store backups in multiple locations, such as offsite storage or cloud services, to ensure data redundancy.
- Develop a disaster recovery plan that Artikels steps for restoring data and services in the event of a disaster.
Security Considerations for Servers
Servers are the backbone of modern businesses and organizations, enabling access to critical data, applications, and services. However, these servers are also prime targets for cyberattacks, making security a paramount concern. Implementing robust security measures is essential to protect sensitive data, maintain business continuity, and prevent costly disruptions.
Server Vulnerabilities
Servers are susceptible to various vulnerabilities that attackers can exploit to gain unauthorized access or disrupt operations. Common vulnerabilities include:
- Operating System Weaknesses: Outdated operating systems and unpatched software can contain security flaws that attackers can exploit.
- Misconfigured Services: Improperly configured services, such as web servers or databases, can expose sensitive information or allow unauthorized access.
- Weak Passwords: Using weak or easily guessed passwords makes it easier for attackers to gain access to server accounts.
- Network Security Gaps: Insufficient network security measures, such as firewalls or intrusion detection systems, can leave servers vulnerable to attacks.
- Malware Infections: Servers can become infected with malware, such as viruses or ransomware, which can steal data, disrupt operations, or demand ransom payments.
Implementing Security Measures
To mitigate these vulnerabilities, it is crucial to implement comprehensive security measures. These measures include:
- Firewall: A firewall acts as a barrier between the server and the external network, blocking unauthorized access and filtering incoming and outgoing traffic.
- Intrusion Detection System (IDS): An IDS monitors network traffic for suspicious activity and alerts administrators to potential threats. It can detect and prevent attacks by identifying malicious patterns in network traffic.
- Access Control: Access control mechanisms restrict access to server resources based on user roles and permissions. This ensures that only authorized individuals can access sensitive data and applications.
- Regular Security Updates: Regularly updating operating systems, software, and firmware patches security vulnerabilities and reduces the risk of exploitation.
- Antivirus and Anti-malware Software: Installing and maintaining antivirus and anti-malware software protects servers from malware infections and prevents data theft or system disruption.
- Data Encryption: Encrypting sensitive data stored on servers helps protect it from unauthorized access even if the server is compromised. Encryption algorithms transform data into an unreadable format, making it inaccessible to unauthorized individuals.
- Security Audits: Regular security audits assess the effectiveness of security measures and identify potential weaknesses that need to be addressed. These audits can help ensure that security controls are up-to-date and effective in mitigating risks.
Protecting Sensitive Data
Protecting sensitive data is paramount for organizations. To safeguard this data, consider the following recommendations:
- Data Loss Prevention (DLP): DLP solutions identify and prevent sensitive data from leaving the organization’s network. They can monitor data transfers, block unauthorized access, and alert administrators to potential data breaches.
- Data Segmentation: Segmenting data into different security zones based on sensitivity levels can limit the impact of a security breach. By restricting access to sensitive data, organizations can reduce the risk of unauthorized access and data theft.
- Data Backup and Recovery: Regularly backing up data and implementing disaster recovery plans ensure that critical data can be restored in case of a server failure or security breach. This helps minimize downtime and data loss.
- Employee Training: Educating employees about security best practices, such as strong password creation, phishing awareness, and data handling protocols, is crucial in preventing security breaches. Employees should be trained to recognize and report suspicious activity to prevent unauthorized access or data loss.
Mitigating Security Risks
Mitigating security risks requires a proactive approach to identifying and addressing potential threats. This includes:
- Security Awareness Training: Regularly training employees on security best practices, phishing awareness, and data handling protocols can significantly reduce the risk of human error-related breaches.
- Vulnerability Scanning: Regularly scanning servers for vulnerabilities helps identify and address security flaws before they can be exploited by attackers. This proactive approach can prevent potential breaches and minimize the impact of security incidents.
- Incident Response Plan: Having a comprehensive incident response plan in place allows organizations to respond effectively to security incidents. This plan should Artikel steps to contain the incident, investigate the cause, and recover from the breach.
Case Studies and Real-World Examples
Servers play a crucial role in various industries and applications, powering everything from websites and online services to critical infrastructure and scientific research. Examining real-world examples of server deployments provides valuable insights into their impact, benefits, and challenges.
E-commerce Platform Scalability
E-commerce platforms rely heavily on servers to handle high traffic volumes, process transactions, and store customer data. A prominent example is Amazon, which utilizes a vast server infrastructure to power its online marketplace. Amazon’s server architecture is designed for scalability and reliability, enabling it to handle millions of requests per second during peak shopping seasons. By leveraging server clusters and load balancing techniques, Amazon ensures a seamless customer experience even during periods of high demand. The success of Amazon’s e-commerce platform highlights the importance of server infrastructure in enabling businesses to scale and meet the demands of a global customer base.
Final Wrap-Up
As we conclude our exploration of the Artikel server, it becomes evident that servers are the unsung heroes of the digital age, silently orchestrating the seamless flow of information and enabling the interconnected world we know. From powering websites and applications to facilitating secure communication and managing data, servers are the backbone of modern infrastructure. This guide has provided a comprehensive overview of server technology, equipping you with the knowledge to understand their vital role in today’s digital landscape.
An outline server acts as a blueprint for your network infrastructure, defining roles and responsibilities for each server. For example, you might choose to utilize a Windows Server 2019 as a domain controller, managing user accounts and security policies across your network.
By creating a comprehensive outline server plan, you can ensure a well-organized and efficient server environment.