HTTP proxy, a fundamental component of the internet, acts as a middleman between your device and the websites you visit. It intercepts your requests, processes them, and then forwards them to the destination server, often providing a layer of security, privacy, and performance optimization. Imagine a bustling marketplace where you need a trusted guide to navigate the crowds and find the best deals – that’s what an HTTP proxy does for your online activities.
These proxies come in various flavors, each tailored to specific needs. Forward proxies, for instance, can enhance security and privacy for individual users, while reverse proxies shield web servers from direct attacks and optimize performance. Understanding the nuances of different proxy types is crucial for selecting the right tool for your specific use case.
How HTTP Proxies Work
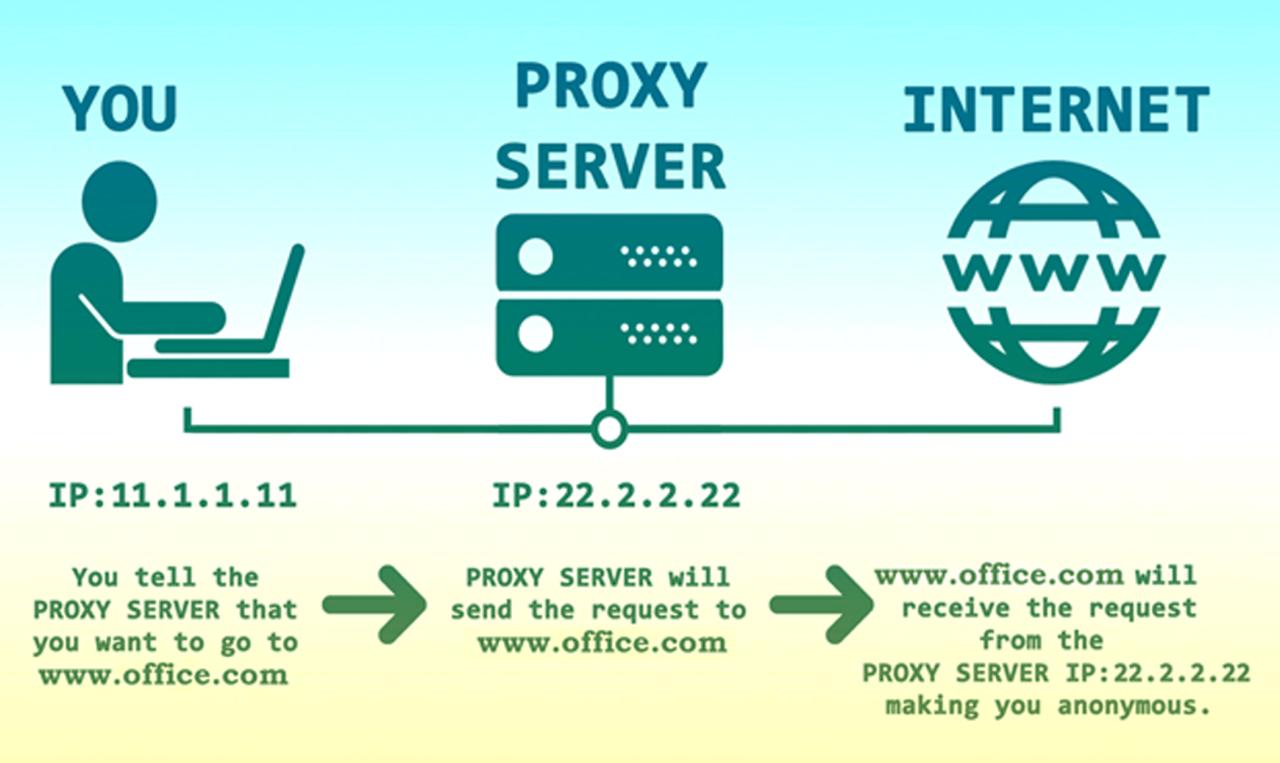
HTTP proxies act as intermediaries between clients and servers, facilitating communication and enhancing network security. They intercept client requests, process them, and forward them to the destination server. After receiving the response, the proxy relays it back to the client.
Communication Flow
The communication flow between clients, proxies, and servers involves a series of steps.
- Client Request: When a client (e.g., a web browser) wants to access a resource on a server (e.g., a website), it sends a request to the proxy server, specifying the desired resource.
- Proxy Request Forwarding: The proxy server then forwards the client’s request to the target server, acting as an intermediary.
- Server Response: The server processes the request and sends a response back to the proxy server.
- Proxy Response Handling: The proxy server receives the response from the server and modifies it (if needed) before relaying it back to the client.
- Client Response: Finally, the client receives the response from the proxy server and displays the requested resource.
Request Forwarding and Response Handling
HTTP proxies handle request forwarding and response handling by modifying the request headers and the response headers.
- Request Forwarding: The proxy server modifies the request headers to reflect the client’s IP address and port. This allows the server to identify the client’s origin and respond accordingly. Additionally, the proxy server can modify the request headers to add or remove specific information.
- Response Handling: The proxy server receives the response from the server and modifies the response headers to reflect the client’s IP address and port. This ensures that the response is delivered to the correct client. The proxy server can also modify the response headers to add or remove specific information, such as caching instructions.
Diagram of an HTTP Proxy
Imagine a diagram with three elements: a client, a proxy server, and a target server. The client sends a request to the proxy server, which then forwards it to the target server. The target server processes the request and sends a response back to the proxy server. Finally, the proxy server forwards the response back to the client.
An HTTP proxy acts as a middleman between your device and the internet, often used to enhance security or bypass geographical restrictions. If you’re looking for a creative outlet, perhaps you’d be interested in diy shoes , where you can personalize your footwear.
Once you’ve finished customizing your shoes, you can use an HTTP proxy to browse the web securely and privately, ensuring your online activity remains protected.
HTTP proxies play a crucial role in facilitating network communication and enhancing security. They act as intermediaries between clients and servers, handling request forwarding, response handling, and various other functions.
Common Use Cases for HTTP Proxies
HTTP proxies are versatile tools with a wide range of applications across various industries and domains. They act as intermediaries between clients and servers, enabling numerous functionalities that enhance security, performance, and functionality. This section explores the common use cases of HTTP proxies and illustrates their impact on different contexts.
Web Browsing
HTTP proxies are frequently used for web browsing, offering several advantages:
- Privacy Enhancement: Proxies can mask a user’s IP address, making it difficult to track their online activities. This is particularly useful for protecting personal information and enhancing privacy while browsing sensitive websites.
- Content Access: Proxies can bypass geographic restrictions imposed by websites or content providers. For example, users in one country can access content that is only available in another country by routing their traffic through a proxy server located in the desired region.
- Security Enhancement: Proxies can act as a security barrier between a user’s device and the internet, filtering malicious content and preventing malware infections. They can also block access to harmful websites or domains, enhancing overall security.
Content Filtering
HTTP proxies are effective tools for content filtering, allowing administrators to control the content accessible by users on a network.
- Parental Control: Proxies can be used to restrict access to inappropriate content, such as adult websites or violent material, for children and teenagers. Parents or guardians can configure proxies to block specific websites or categories of content, ensuring a safe online environment for minors.
- Network Security: Proxies can be used to prevent employees from accessing unauthorized websites or content during work hours. This helps maintain productivity and protect sensitive information from potential leaks.
- Compliance: Proxies can be used to enforce compliance with regulatory requirements, such as preventing access to websites that violate industry standards or regulations. This is particularly important for organizations operating in highly regulated industries.
Caching
HTTP proxies can significantly improve web performance by caching frequently accessed content.
- Reduced Latency: Proxies store copies of web pages, images, and other content locally. When a user requests a cached item, the proxy server delivers it directly, eliminating the need to contact the origin server. This reduces latency and improves page load times.
- Reduced Bandwidth Usage: Caching reduces the amount of data that needs to be transferred between the client and the origin server, saving bandwidth and reducing network congestion.
- Improved Server Performance: Caching reduces the load on origin servers by handling requests for cached content. This improves server performance and availability, especially during peak traffic hours.
Load Balancing
HTTP proxies can distribute traffic across multiple servers, improving website performance and availability.
- Increased Availability: Load balancing ensures that traffic is evenly distributed across all available servers. This reduces the risk of a single server becoming overloaded and becoming unavailable. It also allows for seamless failover if one server fails, ensuring continuous service availability.
- Improved Performance: By distributing traffic across multiple servers, load balancing reduces the response time for users. This improves website performance and user experience.
- Scalability: Load balancing enables websites to scale easily by adding or removing servers as needed. This ensures that websites can handle increasing traffic volumes without compromising performance.
Examples of HTTP Proxy Use Cases
- Corporate Networks: Many corporations use HTTP proxies to control access to the internet for their employees. These proxies can enforce security policies, filter content, and monitor internet usage. This ensures a safe and productive work environment.
- Schools and Universities: Educational institutions use HTTP proxies to manage internet access for students and faculty. These proxies can block inappropriate websites, enforce bandwidth limits, and monitor network activity.
- E-commerce Websites: E-commerce websites often use HTTP proxies for load balancing and content caching. This helps to improve website performance and ensure that customers can access the website smoothly, even during peak traffic hours.
Setting Up and Configuring HTTP Proxies
Setting up and configuring an HTTP proxy server can be a bit technical, but it’s not overly complex. Essentially, you need to install and configure a proxy server software on a machine that will act as the intermediary between your clients and the internet. Then, you need to configure your clients (computers, browsers, or devices) to use this proxy server.
Configuring Proxy Servers
There are various proxy server software options available, each with its own set of features and functionalities. Some popular choices include:
- Squid: A powerful and widely used open-source proxy server, known for its flexibility and performance.
- Apache HTTP Server: A versatile web server that can also function as a proxy server, providing a comprehensive solution.
- Nginx: Another popular open-source web server that can be configured as a proxy server, offering high performance and scalability.
- TinyProxy: A lightweight and easy-to-use proxy server, ideal for smaller deployments.
The configuration process for these servers might differ slightly, but generally involves:
- Installing the software: This typically involves downloading the software package and running the installation script. The installation process is usually straightforward and guided by the software’s documentation.
- Configuring the proxy server: Once installed, you need to configure the proxy server using a configuration file. This file typically defines settings such as the listening port, access control lists, and caching options.
- Starting the proxy server: After configuring the server, you need to start it using the appropriate command. The server will then be listening on the specified port, ready to handle requests.
Configuring Proxy Settings on Different Operating Systems and Browsers
Once the proxy server is set up, you need to configure your clients to use it. This involves modifying the proxy settings on your operating system and web browser.
Configuring Proxy Settings on Windows
To configure proxy settings on Windows, follow these steps:
- Open the Control Panel.
- Go to Network and Internet.
- Click on Internet Options.
- Select the Connections tab.
- Click on LAN settings.
- Check the box for Use a proxy server for your LAN.
- Enter the address of your proxy server in the Address field.
- Enter the port number in the Port field.
- Click OK to save the changes.
Configuring Proxy Settings on macOS
To configure proxy settings on macOS, follow these steps:
- Open System Preferences.
- Click on Network.
- Select the network connection you want to configure.
- Click on Advanced.
- Select the Proxies tab.
- Check the box for Web Proxy (HTTP).
- Enter the address of your proxy server in the Server field.
- Enter the port number in the Port field.
- Click OK to save the changes.
Configuring Proxy Settings on Linux
Configuring proxy settings on Linux can vary depending on the specific distribution and desktop environment. However, the general process involves editing the network configuration files.
- Open a terminal window.
- Edit the appropriate network configuration file. This file might be located in /etc/sysconfig/network-scripts/ or /etc/network/interfaces.
- Add the following lines to the file, replacing proxy_server_address and proxy_server_port with the actual values:
http_proxy=http://proxy_server_address:proxy_server_port
https_proxy=https://proxy_server_address:proxy_server_port
- Save the file and restart the network service.
Configuring Proxy Settings in Web Browsers
Most web browsers allow you to configure proxy settings directly. The steps might differ slightly depending on the browser, but generally involve:
- Open the browser settings or preferences.
- Navigate to the network or proxy settings section.
- Select the option to use a proxy server.
- Enter the address and port number of your proxy server.
- Save the changes.
Troubleshooting Common Configuration Issues
When setting up and configuring a proxy server, you might encounter some common issues. Here are some troubleshooting tips:
- Verify the proxy server address and port: Double-check that you have entered the correct address and port number for your proxy server in both the server configuration and client settings.
- Check the firewall settings: Ensure that your firewall is not blocking the proxy server’s traffic. You might need to configure firewall rules to allow access to the proxy server’s port.
- Restart the proxy server: If you made any changes to the proxy server configuration, restart the server to apply the changes.
- Test the proxy server connection: Use a proxy server testing tool or website to verify that your client can successfully connect to the proxy server.
- Review the proxy server logs: The proxy server logs can provide valuable information about any errors or issues that might be occurring. Check the logs for any error messages or suspicious activity.
Future Trends in HTTP Proxies: Http Proxy
HTTP proxies have been a cornerstone of internet connectivity and security for decades, and their role continues to evolve as the digital landscape transforms. Emerging technologies like web security, cloud computing, and artificial intelligence are poised to significantly impact how HTTP proxies function and are used.
The Rise of Zero-Trust Security, Http proxy
The concept of zero-trust security is gaining momentum, demanding that every connection, regardless of source, be authenticated and authorized before access is granted. This shift towards a more secure and granular approach to network security will have a profound impact on HTTP proxies. HTTP proxies will play a crucial role in implementing zero-trust principles by acting as a central point of control for verifying and enforcing access policies. They will be essential for:
* Enhancing authentication and authorization: HTTP proxies will become more sophisticated in their ability to authenticate users and devices, leveraging advanced authentication methods like multi-factor authentication (MFA) and biometrics.
* Implementing granular access controls: HTTP proxies will enable organizations to define highly specific access rules based on user identity, device type, location, and other factors, ensuring that only authorized users can access sensitive data.
* Detecting and mitigating threats: HTTP proxies will become more proactive in identifying and blocking malicious traffic, leveraging advanced threat intelligence and machine learning algorithms to detect and respond to evolving cyber threats.
Cloud-Native Proxies
Cloud computing has revolutionized how applications are developed and deployed, and HTTP proxies are no exception. Cloud-native proxies are emerging as a new breed of proxies designed to operate seamlessly within cloud environments. They offer several advantages:
* Scalability and Elasticity: Cloud-native proxies can scale up or down automatically to handle fluctuating traffic demands, ensuring optimal performance even during peak usage periods.
* Simplified Deployment and Management: Cloud-native proxies are typically deployed and managed through cloud-based interfaces, making them easier to configure and maintain.
* Integration with Cloud Services: Cloud-native proxies integrate seamlessly with other cloud services, such as load balancers, security services, and monitoring tools.
AI-Powered Proxies
Artificial intelligence (AI) is transforming various industries, and HTTP proxies are not immune to its influence. AI-powered proxies will leverage machine learning algorithms to:
* Optimize Proxy Performance: AI can analyze traffic patterns and user behavior to dynamically adjust proxy configurations, improving performance and efficiency.
* Enhance Security: AI can identify and block malicious traffic in real time, based on continuous learning from past attacks and emerging threats.
* Personalize User Experiences: AI can analyze user preferences and browsing history to provide personalized content and recommendations, enhancing the overall user experience.
The Future of HTTP Proxies
HTTP proxies will continue to be an indispensable part of the internet infrastructure, playing a vital role in ensuring security, performance, and user experience. As technology advances, we can expect to see:
* More sophisticated and intelligent proxies: HTTP proxies will leverage advanced technologies like AI, machine learning, and blockchain to provide even greater security, performance, and efficiency.
* Increased adoption of cloud-native proxies: Cloud-native proxies will become the norm, offering scalability, agility, and cost-effectiveness.
* Greater integration with other technologies: HTTP proxies will be tightly integrated with other technologies, such as firewalls, intrusion detection systems, and content delivery networks, to create comprehensive security and performance solutions.
Outcome Summary
From safeguarding your online activities to optimizing web performance, HTTP proxies play a vital role in the modern digital landscape. As technology evolves, we can expect to see even more innovative applications of proxies, further enhancing our online experiences and shaping the future of the internet.